- About Us
- Expertise Zone
- Success Stories
- Analytics Solution – Investment Bank
- Customer 360 – Retailer
- Data Lineage – Trading Exchange
- Data Quality – Financial Organization
- Leveraging Financial Information – Generative AI
- Data Privacy Program – Financial Organization
- Digital Transformation – Mobility Support
- Digital Transformation – Healthcare
- Work With Us
- Succeed Together
- 250 Main Street, 2nd Floor, USA
- support@example.com
- About Us
- Expertise Zone
- Success Stories
- Analytics Solution – Investment Bank
- Customer 360 – Retailer
- Data Lineage – Trading Exchange
- Data Quality – Financial Organization
- Leveraging Financial Information – Generative AI
- Data Privacy Program – Financial Organization
- Digital Transformation – Mobility Support
- Digital Transformation – Healthcare
- Work With Us
- Succeed Together
Reduce Data Exfiltration Risk
Sensitive Data: The Heart of Your Organization's Security Strategy
Sensitive data, such as Personally Identifiable Information (PII), financial records, intellectual property, and health data, is essential to your organization’s integrity and success. Protecting this data is critical not only for compliance with privacy laws but for maintaining customer trust and safeguarding your competitive advantage. In today’s world, ensuring its security is non-negotiable.
The Consequences of Data Exfiltration: Reputational Damage and Financial Impact
Data exfiltration presents a devastating risk to your business. It can erode customer trust, damage your brand, and lead to costly legal fees, fines, and regulatory penalties. The long-term effects are farreaching, impacting operations and your ability to maintain a strong market position. Proactively addressing data security is vital to mitigate these risks and protect your future.
Data Classification: The First Line of Defense Against Exfiltration
Effective data classification is key to safeguarding your organization’s sensitive information. By categorizing data according to sensitivity, you can implement targeted security measures like encryption and access control. This ensures that your most valuable data is protected and that employees understand the risks, minimizing the potential for accidental leaks or unauthorized access.
Data Exfiltration via Malware and Phishing: The Growing Threats
Cybercriminals often employ malware and phishing tactics to gain access to sensitive data. By tricking employees into revealing credentials or infecting systems with malware, attackers can extract valuable information undetected. Combating these threats requires robust cybersecurity practices, including endpoint protection, phishing awareness training, and continuous network monitoring.
Mitigating Insider Threats: Protecting Against Internal Risks
Insider threats—whether malicious or accidental—pose significant risks to your organization’s data. Employees, contractors, and partners with access to sensitive information can either intentionally or unintentionally cause data breaches. Implementing access controls, robust monitoring, and comprehensive training are essential steps to mitigate these risks and ensure data security from within.
Advanced Tools for Stopping Data Exfiltration: Automation at Its Best
Tools like Microsoft Purview, Proofpoint, and Symantec DLP offer advanced capabilities to detect, prevent, and respond to data exfiltration. These tools automate data classification, real-time monitoring, and security policy enforcement, helping businesses protect sensitive information and stay compliant with privacy regulations.
Simplifying DLP Implementation: Quick, Efficient, and Secure
A Data Loss Prevention (DLP) solution can be easily implemented by starting with sensitive data identification, followed by the creation of DLP policies and the deployment of the right tools. Regular employee training and constant monitoring ensure that your data is protected from internal and external threats, providing a solid foundation for long-term security.
The Power of Encryption: Locking Down Your Sensitive Data
Encryption is one of the most effective methods to prevent data exfiltration. By converting sensitive data into unreadable code, encryption ensures that even if data is intercepted or stolen, it cannot be accessed without the decryption key. Applying encryption to data both in transit and at rest significantly strengthens your organization’s data security posture.
Building a Culture of Security: Employee Awareness and Best Practices
Employee awareness is critical in the fight against data exfiltration. Through regular training and simulated phishing exercises, employees can learn to recognize potential threats and follow best practices to protect sensitive information. A strong culture of security awareness reduces the risk of human error and empowers your team to be proactive in safeguarding your organization.
Protecting Cloud-Based Data: A New Frontier for Data Exfiltration Risks
As businesses move to the cloud, securing cloud-based data is becoming increasingly important. Misconfigurations, weak access controls, and compromised credentials can expose sensitive information. By adopting best practices like multi-factor authentication (MFA) and encryption, and utilizing tools like CASBs, you can protect your cloud environment and prevent unauthorized access to your data.
Making the Case for Data Classification and Retention: Strategic ROI
Data classification and retention aren’t just about compliance—they’re strategic investments that drive cost savings, reduce risks, and improve operational efficiency. By ensuring sensitive data is properly managed and protected, businesses can enhance customer trust and maintain a competitive edge in the marketplace. A strong business case demonstrates the long-term value of a solid data governance strategy.
Key Challenges in a DLP tool implementation
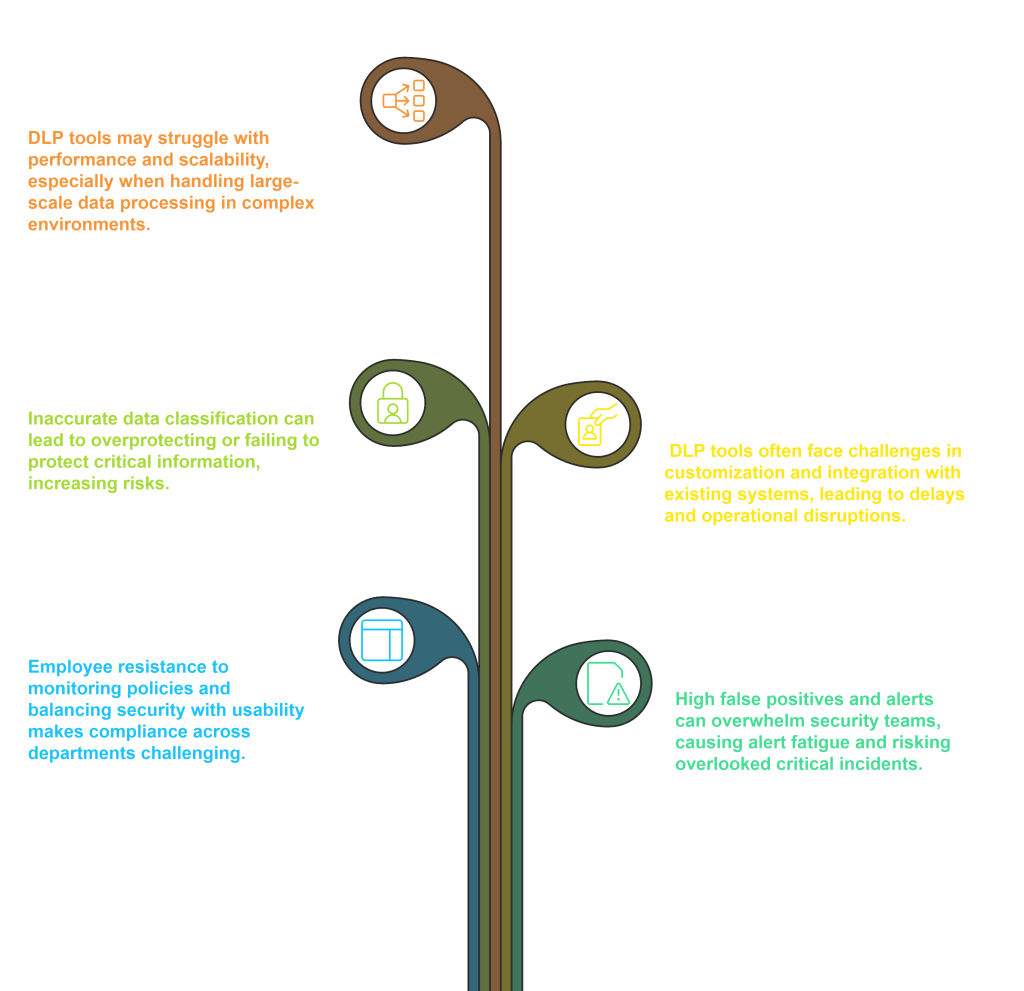
How We can Help
Leveraging our vast experience in implementing Data Loss Prevention (DLP) solutions across diverse industries, we offer unparalleled expertise in navigating complex data environments. We are well-versed in the intricacies of privacy regulations and compliance standards, ensuring that your DLP strategy is not only fully compliant but also optimized for peak performance. Our tailored approach ensures a smooth and impactful implementation, enabling your organization to protect sensitive information, mitigate risks, and drive operational excellence.
