- About Us
- Expertise Zone
- Success Stories
- Analytics Solution – Investment Bank
- Customer 360 – Retailer
- Data Lineage – Trading Exchange
- Data Quality – Financial Organization
- Leveraging Financial Information – Generative AI
- Data Privacy Program – Financial Organization
- Digital Transformation – Mobility Support
- Digital Transformation – Healthcare
- Work With Us
- Succeed Together
- 250 Main Street, 2nd Floor, USA
- support@example.com
- About Us
- Expertise Zone
- Success Stories
- Analytics Solution – Investment Bank
- Customer 360 – Retailer
- Data Lineage – Trading Exchange
- Data Quality – Financial Organization
- Leveraging Financial Information – Generative AI
- Data Privacy Program – Financial Organization
- Digital Transformation – Mobility Support
- Digital Transformation – Healthcare
- Work With Us
- Succeed Together
Phishing Defense
Phishing Explained: A Growing Threat
Phishing is a cyber attack where criminals impersonate trusted entities to trick individuals into revealing sensitive data like passwords or credit card numbers. This can involve deceptive emails, fake websites, and malicious links. Phishing tactics, including spear phishing and whaling, exploit human psychology to bypass technical defenses, making it a widespread and effective method of attack.
Why Phishing Attacks Are Dangerous
Phishing is a low-cost, high-reward strategy for cybercriminals, allowing them to steal data, gain unauthorized access, or deploy malware. The consequences for businesses are severe—financial losses, data breaches, reputational damage, and regulatory fines. Phishing can also pave the way for larger attacks like ransomware, highlighting its importance as a primary threat.
How Anti-Phishing Software Shields Your Organization
Anti-phishing software is essential for blocking phishing attempts before they reach users. With advanced algorithms, it scans emails, URLs, and attachments to identify malicious activity, filtering out phishing and spam emails. Integration with email platforms and web browsers ensures real-time protection against sophisticated attacks, reducing the risk of breaches and financial harm.
Enhanced Protection with Modern Anti-Phishing Tools
Modern anti-phishing software includes key features like real-time URL scanning, AI-driven threat detection, and email authentication protocols (DMARC, DKIM, SPF). These features provide multilayered defense, ensuring your organization is protected from evolving phishing tactics and malware threats. Additionally, integration with endpoint protection further strengthens security.
The Power of Employee Awareness and Training
Technology alone isn’t enough—employee vigilance is critical in preventing phishing attacks. Training programs help staff identify phishing attempts, and phishing simulation exercises test their response. By fostering a culture of security awareness, businesses turn employees into an effective first line of defense against phishing.
Strengthening Defenses Through Phishing Simulation
Phishing simulation software is crucial for strengthening an organization’s anti-phishing efforts by proactively testing and improving employee awareness. These tools mimic real-world phishing attacks, allowing employees to practice identifying and responding to suspicious emails in a safe setting. By consistently exposing staff to realistic threats, organizations can evaluate the success of their training programs and pinpoint areas that need improvement. This hands-on approach not only helps employees become better at spotting phishing attempts but also promotes a culture of ongoing learning and vigilance. When combined with other security measures, like AI-powered threat detection and endpoint protection, phishing simulation tools form a strong, multi-layered defense against ever-evolving cyber threats.
AI-Driven Protection Against Phishing
AI is revolutionizing phishing defense by enabling faster, more accurate detection of threats. Machine learning algorithms analyze data patterns to identify phishing attempts in real time, providing proactive protection. AI can also adapt to new phishing tactics, automating responses like quarantining suspicious emails and blocking harmful websites, reducing IT workload.
The Power of Multi-Factor Authentication (MFA)
Even if phishing attacks succeed in stealing credentials, Multi-Factor Authentication (MFA) adds an essential layer of protection. By requiring additional verification, such as a one-time code or biometric scan, MFA prevents attackers from easily accessing systems—even with compromised credentials. It’s an effective measure to mitigate phishing risks and protect sensitive data.
Phishing Threats in the Cloud
With the growing shift to cloud environments, phishing attacks targeting cloud credentials are on the rise. Attackers aim to steal login details for platforms like Microsoft 365, Google Workspace, and AWS. To counter this, businesses must implement cloud-specific security measures, such as conditional access policies and session monitoring, to safeguard against unauthorized access and breaches.
Responding to Phishing Incidents with a Plan
Despite precautions, some phishing attacks may succeed. A strong incident response plan enables rapid detection, containment, and recovery from phishing incidents. Steps like resetting compromised credentials and isolating affected systems are essential. Regular testing and updates ensure businesses are prepared and can minimize the impact of successful attacks.
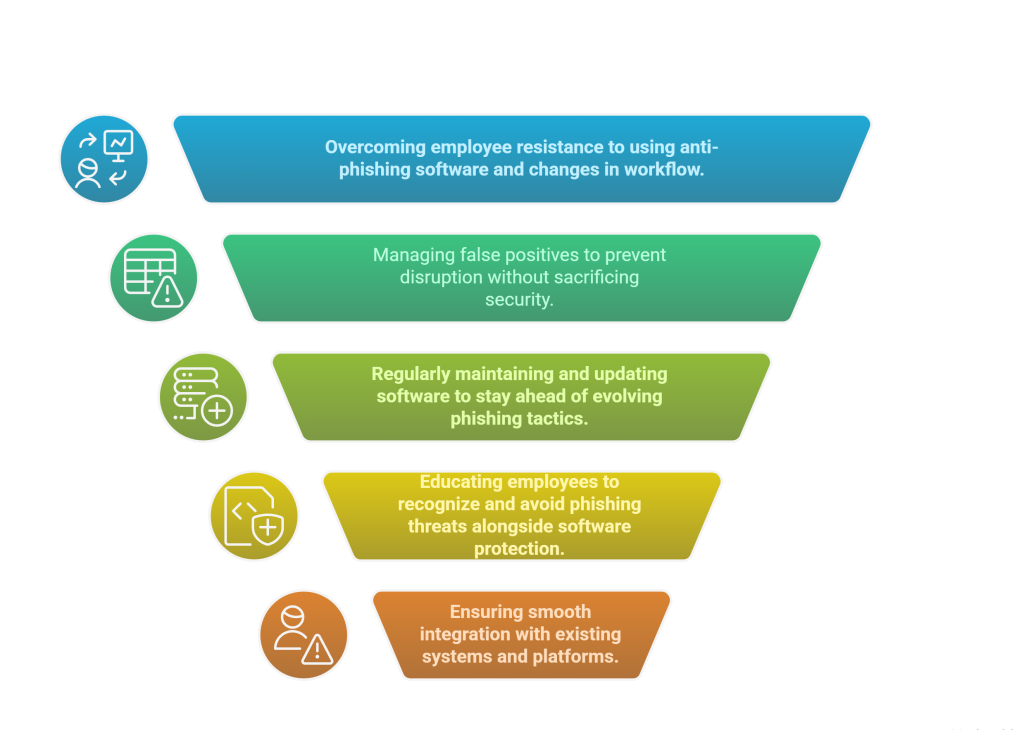
Top five Challenges in Implementing an Anti-phishing Strategy:
How We can Help
Selecting the right anti-phishing and phishing simulation software can be challenging, as it requires consideration of factors such as cost, benefits, protection, cloud compatibility, and organizational size. With our expertise, we guide you through the selection and implementation process to ensure you derive maximum value. Additionally, we design impactful phishing simulation campaigns and customized training programs to enhance your organization’s defenses.
